Changelog
-
You can now install the Netlify MCP on Cursor with a single click.
Check out our docs on the Netlify MCP server here.
-

The Netlify MCP Server enables AI agents to deploy applications directly from your editor. Built on the Model Context Protocol, agents can now complete the full development cycle from code to production.
-

Netlify is now the official deployment partner for Vite, plus introducing our new Vite plugin. Access the Netlify platform directly into your local dev environment.
-
Angular 20 is now fully supported on Netlify with zero configuration required.
What’s new
-
Full Angular 20 compatibility: Deploy Angular 20 projects with all the latest features including stable signals APIs, zoneless change detection in developer preview, and incremental hydration.
-
Updated Angular template: We’ve refreshed our Angular starter template to showcase Angular 20’s capabilities, including the new control flow syntax and simplified component naming conventions.
-
Optimized SSR support: Angular 20’s stable incremental hydration and route-level rendering modes work with Netlify’s edge network for faster, more efficient server-side rendering.
How to get started
Add your existing Angular 20 project by connecting your Git repository–or deploy our template–no configuration changes needed. For new projects, try our updated template with Angular 20’s latest features.
If you’re planning to upgrade from version 18 or earlier, check out our guidance on the Angular runtime.
-
-
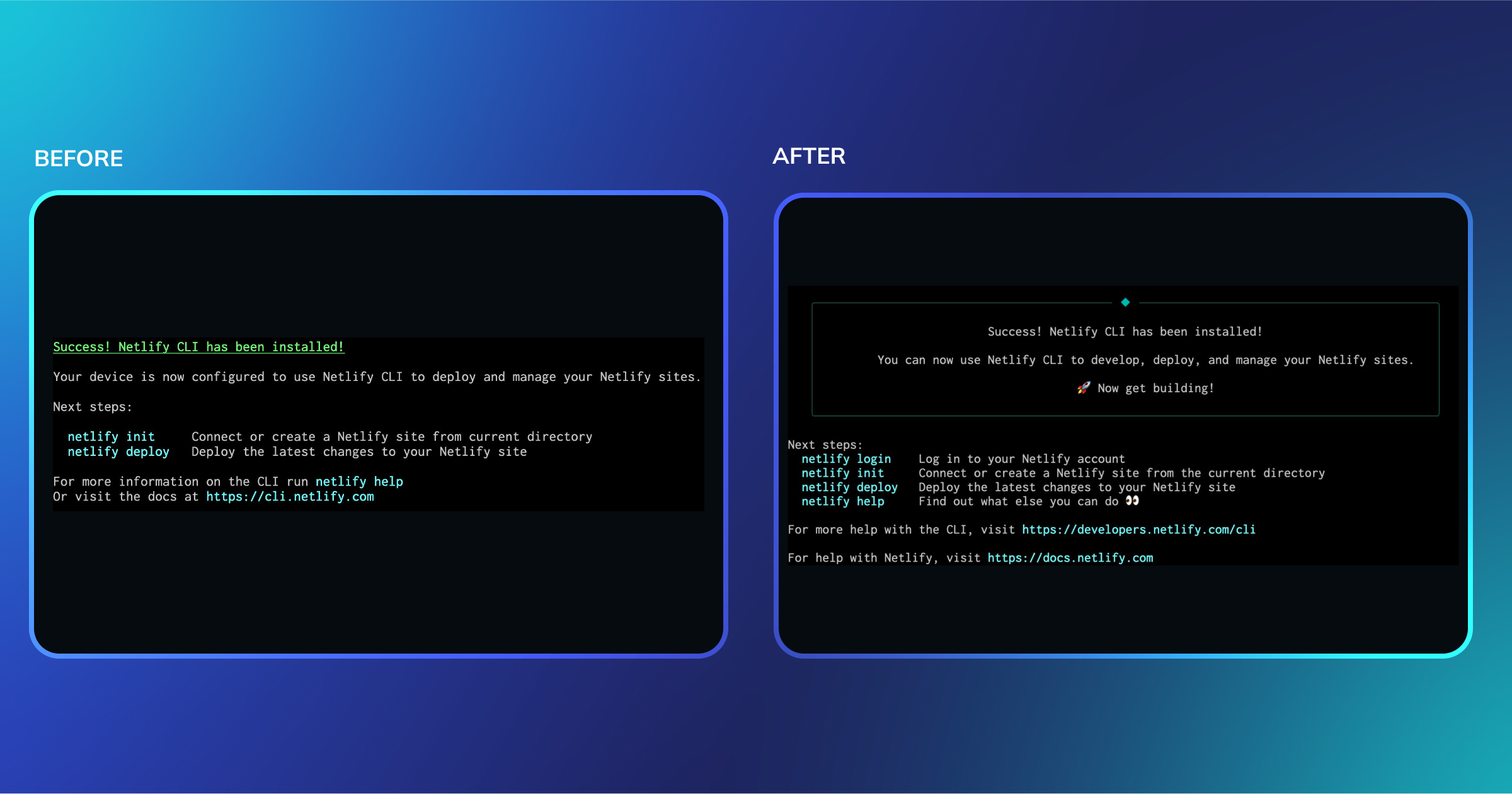
Netlify CLI 21.4.1 has a cleaner look, simplified workflows, and a new command.
Install the latest version:
npm install netlify-cli -g # or yarn global add netlify-cliOnboard to Netlify projects with
netlify clonecommandPull an existing Netlify project locally from its repo with one command:
netlify clone <repository-url>Clones the repo and links it to the right Netlify site–ideal for onboarding or switching projects.
Builds are included with
netlify deployThe deploy command now runs a build step by default, eliminating separate build commands.
Instead of
netlify build && netlify deployornetlify deploy --build, simply run:netlify deployTo deploy without building, use netlify
deploy --no-build.Smarter manual setup
netlify initnow auto-detects your framework and suggests the right build settings. It’ll even help you create a netlify.toml if you don’t have one.Better updates and onboarding
Additional improvements include:
- Better update notifications with links to release notes
- Improved onboarding guidance with clearer next steps and resource links
- Reorganized help command with better documentation references
-
The Next.js team recently disclosed CVE-2025-32421, a low-severity vulnerability allowing for CDN cache poisoning in some scenarios.
The engineering team at Netlify has confirmed that all Next.js sites on Netlify are not vulnerable. The vulnerability requires use of a CDN that may cache responses without explicit Cache-Control headers, but Netlify’s CDN never does so.
As a general security precaution, we recommend upgrading to the latest versions of the Next.js framework and allowing automatic updates of the OpenNext Netlify Next.js adapter.
-

Discover the new Netlify Cache API beta. Built on web standards, it lets developers cache fetch requests in serverless and edge functions. Works seamlessly with any framework (or without one) for faster, more resilient apps.
-
The following versions of Node.js have reached their official end of life. Node.js v14 on February 16, 2023 Node.js v16 on August 9, 2023 It is also worth noting that the following version is also about to reach its end of life date. Node.js v18 on…
-
We are aware of recently disclosed vulnerabilities affecting React Router and Remix:
- CVE 2025-31137 (React Router 7 and Remix): Spoof request path allowing certain access control bypasses
- CVE-2025-43864 (React Router 7 only): Cache poisoning leading to unusable responses
- CVE-2025-43865 (React Router 7 only): Cache poisoning with arbitrary data
Impact on Netlify sites:
- CVE 2025-31137: Sites on Netlify are not vulnerable, because the Netlify CDN cache varies on the query string by default, and Remix and React Router sites on Netlify do not use the impacted Express package.
- CVE-2025-43864: Sites on Netlify using React Router 7.2.0 to 7.5.1 were vulnerable until 04/27 3:00 UTC. However, exploitation requires all of the following conditions for a given URL to be poisonable:
- The site must not be using React Router’s SPA mode.
- The page or loader must be explicitly setting caching headers.
- A malicious request would need to be the first request to reach the cache (such as immediately after a deploy or cache invalidation).
- CVE-2025-43865: Sites on Netlify using React Router 7.0.0 to 7.5.1 were vulnerable until 04/27 3:00 UTC. However, exploitation requires all of the following conditions for a given URL to be poisonable:
- The page or loader must be explicitly setting caching headers.
- A malicious request would need to be the first request to reach the cache (such as immediately after a deploy or cache invalidation).
We strongly recommend upgrading to the latest versions of React Router (7.5.2).
Given these specific requirements, the number of vulnerable Netlify sites is low. However, out of an abundance of caution, our engineering team is actively rolling out a mitigation to further protect against these vulnerabilities. We will continue to monitor the situation and will provide updates as our work progresses.
Update: As of 2025-04-27 3:00 AM UTC, a mitigation has been rolled out to the Netlify CDN for all vulnerable sites.